The Azure Load Balancer edition.
In part 1 we looked at the public IP of a single Windows or Linux VM. If we want to scale or make systems high available you will quickly start looking at the Azure Load Balancer.
There are 2 versions / sku’s of the Azure Load Balancer: Basic and Standard. The basic version has been around from early Azure times. The Standard Version was released in 2017 and has some nice features like: HA Ports, support for Availability Zones, more flexible policies for outbound connections, … As an added bonus any change on the configuration is much quicker (<30 seconds compared to the 60+ seconds for the Basic Azure Load Balancer)
Besides this overview you can find more information on the Microsoft Azure documentation site:
Outbound connections
Now back to the subject of this post and so what about outbound connections? Suppose we have a setup with 2 VM’s and an Azure Load Balancer. What would be the public ip used when connecting to a website from on of these VM’s? There are two options possible:
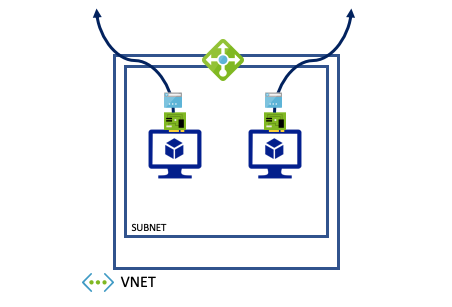
- The VM has a public IP address on the network interface (Instance level public IP): Regardless of being connected to any Azure Load Balancer the outgoing public IP will be the public IP address connected to the networking interface. The connections are using Source NAT (SNAT). If your VM is a firewalll (NVA) you can hide NAT (PAT) behind the private IP of the VM and a such provide internet access for multiple servers behind the firewall.
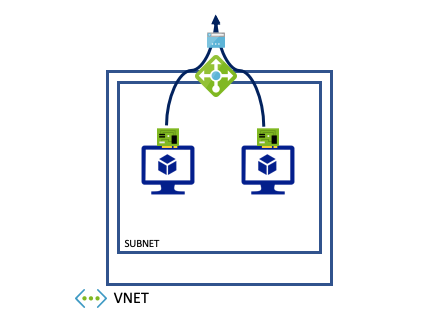
- VM has no instance level public IP address and is connected to an Azure Public Load Balancer: Azure will in this case use the public IP addresses configured on the public load balancer for all outgoing connections.
- It will use port address translation (PAT) to map multiple private IPs behind the public IP(s).
- The Load Balancer will only NAT and process TCP and UDP traffic. This includes IPSEC traffic when it uses NAT-T over UDP 4500 for transport of the data.
- The Load Balancer will only forward and NAT traffic if there is an inbound rule for the protocol (1 needed for TCP and 1 needed for UDP).
- On the Standard Load balancer you can disable outbound SNAT per configured frontend public IP address.
- Watch out for port exhaustion! By default only 1024 ports are reserved per public IP address which is very limited compared to the standard 65k ports. You can use outbound rules to optimize this.
I hope this gives you a short overview of what to expect for your outbound connections in Microsoft Azure!
[…] will explain this in in part 2 of this […]